Deploying AD RMS in a Test Environment
We recommend that you use the steps provided in the “Windows Server Active Directory Rights Management Services Step-by-Step Guide” before completing the steps in this guide. Step-by-step guides are not necessarily meant to be used to deploy
Windows Server® features without additional documentation and should be used with
discretion as a stand-alone document.
Upon completion of this Step-by-Step guide, you will have a working AD RMS test lab environment configured for use in an extranet scenario. You can then test and verify AD RMS extranet functionality through the simple task of restricting permissions on a
Microsoft Office Word 2007 document and attempting to open this document from a client computer that is not part of your organization’s network.
The test environment described in this guide includes six computers that use the following operating systems, applications, and services:
![]()
Note
You will also need a USB flash drive or another medium to copy the files from the
AD RMS-enabled client to the AD RMS-enabled extranet client.
Computer Name | Operating System | Applications and Services |
ADRMS-SRV | Windows Server 2008 | AD RMS, Internet Information Services (IIS) 7.0, Message Queuing, and Windows Internal Database |
CPANDL-DC | Windows Server 2003 with Service Pack 1 (SP1) | Active Directory, Domain Name System (DNS) |
![]()
Computer Name | Operating System | Applications and Services |
ADRMS-DB | Windows Server 2003 with SP1 | Microsoft SQL Server™ 2005 Standard Edition |
ISA-SRV | Windows Server 2003 with SP1 Note This computer must have two network adapters so that ISA Server 2006 can distinguish between the public and private IP addresses. | Microsoft ISA Server 2006 Standard Edition |
ADRMS-CLNT | Windows Vista™ | Microsoft Office Word 2007 Enterprise Edition |
ADRMS-EXCLNT | Windows Vista | Microsoft Office Word 2007 Enterprise Edition |
The first five computers in the table form a private intranet and are connected through a common hub or Layer 2 switch. Additionally, ISA-SRV has a second network adapter installed that is exposed to the Internet. This allows for the ISA Server to accept requests from the Internet and forward them to the AD RMS server. ADRMS-EXCLNT is a computer that is not part of the same network. This configuration can be emulated in a virtual server environment if desired.
This step-by-step exercise uses private addresses throughout the test lab configuration. The private network ID 10.0.0.0/24 is used for the intranet. The domain controller is named CPANDL-DC for the domain named cpandl.com. ADRMS-EXCLNT is configured with an IP address of 10.0.100.2/24 in order to simulate a client computer on an extranet. The following figure shows the configuration of the test environment:
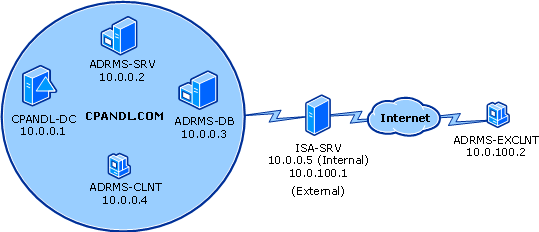
![]()
Note
In a production environment, the ISA server’s external address would be an IP address available to the Internet, giving extranet users the ability to consume rights-protected content.
Step 1: Configuring AD RMS to Work in an Extranet
![]()
In addition to the steps outlined in the “Windows Server Active Directory Rights
Management Services Step-by-Step Guide,” you must also do the following:
• Configure the extranet cluster URL in the Active Directory Rights Management
Services console.
• Export the server authentication certificate, including the private key, on ADRMS- SRV. This will be imported into the Personal certificate store on the ISA server (ISA- SRV).
In order for users who are not connected to your organization’s internal network to consume rights-protected content, you must configure the AD RMS extranet cluster URLs. These URLs are included in the AD RMS client licensor certificate and published with all rights-protected content. These URLs should be an address that is available to all computers on the Internet.
![]()
Note
You must configure the extranet cluster URLs before you can rights-protect content. If you already have rights-protected content, the AD RMS-enabled client must download a new client licensor certificate that includes the extranet cluster URL.
Configuring the extranet cluster URLs is done through the Active Directory Rights Management Services console. You should follow these steps to accomplish this task:
![]()
To configure the AD RMS extranet cluster URLs
1. Log on to ADRMS-SRV as CPANDL\ADRMSADMIN.
2. Click Start, point to Administrative Tools, and then click Active Directory
Rights Management Services.
3. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue.
4. Right-click ADRMS-SRV (Local), and then click Properties.
5. Click the Cluster URLs tab, and then select the Extranet URLs check box.
6. In the Licensing box, select https://, and then type adrms-srv.cpandl.com.
7. In the Certification box, select https://, and then type adrms-srv.cpandl.com.
8. Click OK.
Next, export the ADRMS-SRV server authentication certificate with its private key. This is required so that ISA-SRV can pass HTTPS requests from ADRMS-EXCLNT to the
AD RMS cluster.
![]()
To export the ADRMS-SRV server authentication certificate with private key
1. Click Start, type mmc.exe, and then press ENTER.
2. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue.
3. Click File, and then click Add/Remove Snap-in.
4. Click Certificates, and then click Add.
5. Select the Computer account option, and then click Next.
6. Click Finish, and then click OK.
7. Expand Certificates (Local Computer), expand Trusted Root Certification
Authorities, and then click Certificates in the console tree.
8. Right-click ADRMS-SRV.cpandl.com, point to All Tasks, and then click Export.
9. On the Welcome to the Certificate Export Wizard page, click Next.
10. Select the Yes, export the private key option, and then click Next.
11. On the Export File Format page, click Next, accepting the default selections.
12. In the Password and Type and confirm password boxes, type the same strong password, and then click Next.
13. In the File name box, type \\adrms-db\public\adrms-srv_with_key.pfx, and then click Next.
14. Click Finish.
15. Click OK, confirming that the export was successful.
Step 2: Installing and Configuring ISA- SRV
![]()
ISA Server 2006 Standard Edition is an integrated edge security gateway that can be used with AD RMS to restrict Internet access to the AD RMS cluster. The ISA server handles all requests from the Internet to the AD RMS extranet cluster URLs and passes them to the AD RMS cluster, when necessary.
To install and configure ISA Server 2006 Standard Edition to work with AD RMS, you must complete the following steps:
• Configure the ISA Server (ISA-SRV)
• Publish AD RMS cluster to extranet
Configure the ISA Server (ISA-SRV)
First, install Windows Server 2003 on a stand-alone server.
![]()
To install Windows Server 2003, Standard Edition
1. Start your computer by using the Windows Server 2003 product CD.
2. Follow the instructions that appear on your computer screen, and when prompted for a computer name, type ISA-SRV.
Next, configure TCP/IP properties so that ISA-SRV has a static IP address of 10.0.0.5 and preferred DNS server with IP address 10.0.0.1 on the first network adapter. On the second network adapter, use 10.0.100.1 as the IP address.
![]()
To configure TCP/IP properties on ISA-SRV
1. Log on to ISA-SRV as a member of the local Administrators group.
2. Click Start, point to Control Panel, point to Network Connections, click Local
Area Connection, and then click Properties.
3. On the General tab, click Internet Protocol (TCP/IP), and then click Properties.
4. Click the Use the following IP address option. In the IP address box, type 10.0.0.5. In the Subnet mask box, type 255.255.255.0. In the Preferred DNS server box, type 10.0.0.1.
5. Click OK, and then click Close to close the Local Area Connection Properties dialog box.
6. Click Start, point to Control Panel, point to Network Connections, click Local Area Connection 2, and then click Properties.
7. On the General tab, click Internet Protocol (TCP/IP), and then click Properties.
8. Click the Use the following IP address option. In the IP address box, type 10.0.100.1. In the Subnet mask box, type 255.255.255.0.
9. Click OK, and then click Close to close the Local Area Connection 2 Properties dialog box.
Next, join ISA-SRV to the cpandl.com domain.
![]()
To join ISA-SRV to the cpandl.com domain
1. Click Start, right-click MyComputer, and then click Properties.
2. Click the Computer Name tab, and then click Change.
3. In the Computer Name Changes dialog box, select the Domain option, and then type cpandl.com.
4. Click More, and type cpandl.com in Primary DNS suffix of this computer box.
5. Click OK, and then click OK again.
6. When a Computer Name Changes dialog box appears prompting you for administrative credentials, provide the credentials for CPANDL\Administrator, and then click OK.
7. When a Computer Name Changes dialog box appears welcoming you to the cpandl.com domain, click OK.
8. When a Computer Name Changes dialog box appears telling you that the computer must be restarted, click OK, and then click Close.
9. Click Restart Now.
Next, import the server authentication certificate that contains the private key into the Trusted Certification Authorities store on ISA-SRV.
![]()
To import the server authentication certificate to the ISA-SRV computer
1. Log on to ISA-SRV with as a member of the local Administrators group.
2. Click Start, click Run, type mmc.exe, and then press ENTER.
3. Click File, and then click Add/Remote Snap-in.
4. Click Add, select Certificates, and then click Add.
5. Select the Computer Account option, click Next, and then click Finish.
6. Click Close, and then click OK.
7. Expand Certificates, and then expand Personal.
8. Right-click Certificates in the console tree, point to All Tasks, and then click Import.
9. On the Welcome to the Certificate Import wizard page, click Next.
10. In the File name box, type \\adrms-db\public\adrms-srv_with_key.pfx, click
OK, and then click Next.
11. Type the password used to export the certificate, and then click Next.
12. Click Next, and then click Finish.
13. Click OK confirming that the import was successful.
14. Close the Certificates console.
Finally, install ISA Server 2006 Standard Edition.
![]()
To install ISA Server 2006 Standard Edition
1. Log on to ISA-SRV as a member of the local Administrators group.
2. Insert the ISA Server 2006 Standard Edition product CD.
3. Click Install ISA Server 2006.
4. On the Welcome to the Installation Wizard for Microsoft ISA Server 2006
page, click Next.
5. Select the I accept the terms in the license agreement option, and then click Next.
6. Type your ISA Server product key in the Product Serial Number box, and then click Next.
7. Select the Typical option, and then click Next.
8. Click Add, click Add Adapter, select the Local Area Connection check box, click OK, and then click OK again.
9. Click Next three times, and then click Install.
10. When the installation is complete, click Finish.
11. Click OK. Read the information if desired, and then close Internet Explorer.
12. Click Exit to close Microsoft ISA Server 2006 Setup.
Publish AD RMS cluster to extranet
ISA Server 2006 Standard Edition requires that a Web listener be configured for a specified port. In this guide, you use TCP port 443 (SSL) in order to help make data transmission secure between the clients and ISA server. In this section, you publish the AD RMS Web site through the ISA server. This involves publishing the AD RMS extranet cluster URL to this ISA Server and then allowing the ISA server to pass the user credentials directly to the AD RMS server. Because a self-signed certificate is used for the AD RMS cluster in this guide, you must move it from the Personal certificate store to the Trusted Certification Root Authorities store.
First, publish the AD RMS cluster on ISA-SRV.
![]()
To publish AD RMS in ISA Server 2006 Standard Edition
1. Click Start, point to All Programs, point to Microsoft ISA Server, and then click
ISA Server Management.
2. Expand ISA-SRV, and then click Firewall Policy.
3. Click the Tasks tab, and then click Publish Web Sites.
4. In the Web publishing rule name box, type AD RMS Extranet, and then click Next.
5. Click Next twice accepting the default selections.
6. Select the Use SSL to connect to the published Web server or server farm
option, and then click Next.
7. In the Internal Site Name box, type adrms-srv.cpandl.com.
8. Select the Use a computer name of IP address to connect to the published server check box, type 10.0.0.2 in the Computer name or IP address box, and then click Next.
9. In the Path (optional) box, type /*, select the Forward the original host header instead of the actual one specified in the Internal site name field on the previous page check box, and then click Next.
10. In the Public name box, type adrms-srv.cpandl.com, and then click Next.
11. Click New to create a new Web listener.
12. In the Web listener name box, type HTTPS Port 443, and then click Next.
13. Select the Require SSL secured connections with clients option, and then click Next.
14. Select the External check box, and then click Next.
15. Select the Use a single certificate for this Web listener option, and then click Select Certificate.
16. Click the ADRMS-SRV.cpandl.com certificate, click Select, and then click Next.
17. In the Select how clients will provide credentials to ISA Server box, select
No Authentication, click Next, and then click Next again.
18. Click Finish to close the New Web Listener Wizard.
19. Click Next.
20. Click No delegation, but client may authenticate directly, and then click Next.
21. Click Next to apply this Web publishing rule to all users.
22. Click Finish.
23. Click Apply to save changes and update your configuration, and then click OK. Finally, move the ADRMS-SRV server authentication certificate from the Personal
certificate store to the Trusted Root Certification Authorities store:
![]()
To move the ADRMS-SRV server authentication certificate
1. Click Start, and then click Run.
2. Type mmc.exe, and then click OK.
3. Click File, and then click Add/Remove Snap-in.
4. Click Add, click Certificates, click Add, select the Computer account option, and then click Next.
5. Click Finish, click Close, and then click OK.
6. Expand Certificates (Local computer), expand Personal, and then expand
Trusted Root Certification Authorities.
7. Click Certificates under Personal in the console tree.
8. Select the ADRMS-SRV.cpandl.com certificate in the details pane and drag it to the Certificates folder under Trusted Root Certification Authorities.
9. Close the Certificates console.
Step 3: Configuring AD RMS Extranet
Client
![]()
To configure the AD RMS extranet client computer (ADRMS-EXCLNT), you must install Windows Vista, configure TCP/IP properties, create an entry in the local HOSTS file, import the ADRMS-SRV server authentication certificate, and then install an AD RMS enabled application. In this example, Microsoft Office Word 2007 is installed on ADRMS- EXCLNT.
![]()
To install Windows Vista
1. Start your computer using the Windows Vista product CD.
2. Follow the instructions that appear on your screen, and when prompted for a computer name, type ADRMS-EXCLNT.
Next, configure TCP/IP properties so that ADRMS-EXCLNT has a static IP address of 10.0.100.2.
![]()
To configure TCP/IP properties
1. Click Start, click Control Panel, click Network and Internet, double-click Network and Sharing Center, click Manage Network Connections in the left pane, right-click Local Area Connection, and then click Properties.
2. On the Networking tab, click Internet Protocol Version 4 (TCP/IPv4), and then click Properties.
3. Select the Use the following IP address option. In IP address, type 10.0.100.2, in Subnet mask, type 255.255.255.0.
4. Click OK, and then click Close to close the Local Area Connection Properties
dialog box.
5. Close the other open windows and return to the desktop.
In this guide, a test environment without an external DNS server is used. In order for the extranet cluster URLs to resolve to its appropriate IP address, you must create a manual entry in the HOSTS file that points to ISA-SRV.
![]()
Note
In a production environment, this step is not required because the extranet client computer’s Internet Service Provider will handle the DNS resolution.
![]()
To create an entry in the HOSTS file for AD RMS extranet cluster URL
1. Log on to ADRMS-EXCLNT as a member of the local Administrators group.
2. Click Start, point to All Programs, click Accessories, and then click Notepad.
3. Within Notepad, click File, and then click Open.
4. Navigate to C:\windows\System32\drivers\etc\HOSTS, and then click Open.
![]()
Note
To show the HOSTS file, when you get to the etc folder you must select
All Files (above the Open button).
5. On a new line at the bottom of the file, type 10.0.100.1 adrms-srv.cpandl.com.
6. Save and close the HOSTS file.
Next, import the ADRMS-SRV server authentication certificate into the Trusted Root Certification store on ADRMS-EXCNT. This is only required when using self-signed certificates. In a production environment, the certificate should be trusted by a certification authority.
17
![]()
To import the server authentication certificate to the ADRMS-EXCLNT computer
1. Log on to ADRMS-EXCLNT with a user account that is a member of the local
Administrators group.
2. Click Start, point to All Programs, and then click Internet Explorer.
3. In the Address bar, type https://adrms- srv.cpandl.com/_wmcs/licensing/license.asmx, and then press ENTER.
4. On the Certificate Error: Navigation Blocked Web page, click Continue to this website (not recommended).
5. In the User name box, type CPANDL\srailson. In the Password box, type the password for Stuart Railson, and then click OK.
6. In the Address Bar, click Certificate Error, and then click View Certificates.
7. On the Certificate Information page, click Install Certificate.
8. On the Welcome to the Certificate Import Wizard page, click Next.
9. Select the Place all certificates in the following store option, click Browse, click Trusted Root Certification Authorities, and then click OK.
10. Click Next, and then click Finish.
11. Click Yes, accepting the security warning. This only happens because self- signed certificates are used.
12. Click OK, confirming that the certificate import was successful.
13. Click OK to close the Certificate Information window.
14. Close Internet Explorer.
Finally, install Microsoft Office Word 2007 Enterprise.
![]()
To install Microsoft Office Word 2007 Enterprise
1. Double-click setup.exe from the Microsoft Office 2007 Enterprise product CD.
2. Click Customize as the installation type, set the installation type to Not Available for all applications except Microsoft Office Word 2007 Enterprise, and then click Install Now. This might take several minutes to complete.
![]()
Important
Only the Ultimate, Professional Plus, and Enterprise editions of Microsoft Office 2007 allow you to create rights-protected content. All editions will allow you to consume rights-protected content.
Step 4: Verifying AD RMS Functionality using ADRMS-CLNT
![]()
To verify the functionality of the AD RMS deployment, you will log on to ADRMS-CLNT as Nicole Holliday and then restrict permissions on a Microsoft Word 2007 document so that Stuart Railson is only able to read the document but unable to change, print, or copy. You will then copy this document to a removable device (for example, a USB flash drive) and log on to a client computer that is not part of the organizational network, such as a home computer. In this example, ADRMS-EXCLNT serves as the home computer. After the file is copied to the USB flash drive, Stuart Railson logs on to the extranet client computer (ADRMS-EXCLNT) and verifies that he is able to open the rights-protected document
from the USB flash drive.
![]()
Note
A USB flash drive is not required in this scenario. Any means of getting the document to the extranet client computer will work, such as attaching the document to an e-mail message and sending it to Stuart. In that example, Stuart would then open the document contained in the e-mail message on the extranet client computer.
Use the following steps to restrict permissions on a Microsoft Word document:
![]()
To restrict permissions on a Microsoft Word document
1. Log on to ADRMS-CLNT as Nicole Holliday (cpandl\nhollida).
2. Click Start, point to All Programs, click Microsoft Office, and then click
Microsoft Office Word 2007.
3. Type This is a test of AD RMS Extranet functionality.into the blank document page, click the Microsoft Office Button, point to Prepare, point to Restrict Permission, and then click Restricted Access.
4. Select the Restrict permission to this document check box.
5. In the Read box, type [email protected], and then click OK to close the Permission dialog box.
6. Click the Microsoft Office Button, click Save As, and then save the file as
ADRMS-TST.
7. Copy ADRMS-TST.docx to a USB flash drive.
8. Log off as Nicole Holliday.
Finally, open the document, ADRMS-TST.docx, on ADRMS-EXCLNT from the USB flash drive.
![]()
To view a protected document
1. Log on to ADRMS-EXCLNT with the local user account that you want to use for consuming the rights-protected document.
![]()
Caution
Once this document has been consumed, any other user who logs on to the computer with the same user account will also be able to consume the document.
2. Insert the USB flash drive, and then double-click the ADRMS-TST.docx file.
3. In the User name box, type cpandl\srailson. In the Password box, type the password for Stuart Railson, and then click OK.
The following message appears: “Permission to this document is currently restricted. Microsoft Office must connect to https://adrms- srv.cpandl.com/_wmcs/licensing to verify your credentials and download your permissions.”
4. Click OK.
The following message appears: “You are attempting to send information to an Internet site (https://adrms-srv.cpandl.com) that is not in your Local, Intranet, or Trusted zones. This could pose a security risk. Do you want to send the information anyway?”
5. Click Yes.
The following message appears: “Verifying your credentials for opening content with restricted permissions…“.
6. When the document opens, click the Microsoft Office Button. Notice that the Print option is not available.
7. Click View Permission in the message bar. You can see that [email protected] (Stuart Railson) has been restricted to so that he can only read the document.
8. Click OK to close the My Permissions dialog box, and then close Microsoft Word.
You have successfully deployed and demonstrated the functionality of AD RMS in an extranet, using the simple scenario of applying restricted permissions to a Microsoft Word 2007 document. You can also use this deployment to explore some of the additional capabilities of AD RMS through additional configuration and testing.